Tag Archives: Cyber Capabilities
Detecting and Identifying Insider Threats. 2022 Best
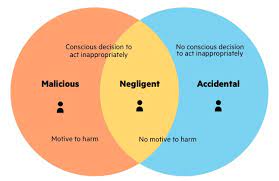
This paper focuses on detecting and identifying insider threats. Firstly, you should provide a background and introduction for implementation of IT/Cyber Capabilities to Detect Insider Threats.
Detecting and Identifying Insider Threats.
Provide a Background and Introduction for Implementation of IT/Cyber Capabilities to Detect Insider Threats. This assignment is to construct an introduction for your topic. Follow this outline to address required components: 1. Include an introduction heading 2. Begin by briefly describing your topic to establish the main ideas and context. 3. Next, orient the reader to the basic concepts about your topic presented in the problem and purpose statements. 4. Next, describe the facts and relevant context as a foundation leading to the study problem and purpose.
Detecting and Identifying Insider Threats.
Focusing on your area of research interest, briefly laying the groundwork for what has been done in the area and why the area is of important social or practical concern, or of theoretical interest. 5. Last, present an overview explaining why this research topic is currently of interest. 6. Include appropriate, recent, and scholarly sources to support each assertion. Support your assignment with at least five scholarly resources. In addition to these specified resources, other appropriate scholarly resources, including older articles, may be included.
Detecting and Identifying Insider Threats.
Length: 4-5 pages, not including title and reference pages Your assignment should demonstrate thoughtful consideration of the ideas and concepts presented in the course by providing new thoughts and insights relating directly to this topic. Your response should reflect scholarly writing and current APA standards. https://youtu.be/nfgflVnD7hE






